Hacker Engineering
Below we list our best services
Enable greater smart code collaboration. HAiCKER Copilot’s the newest HACKER member of your team. You can ask general programming questions, make your code secure or very specific ones about your codebase to get answers fast, learn your way around, explain a mysterious regex, or get suggestions on how to improve legacy code.
See all plansE-MAIL encrypted is a secured private email service with end-to-end encryption to secure your communications, it's ensures no one (not even We, Hackers & Engineers) can access your e-mails.
See all plansOur VPN encrypt your internet traffic through an encrypted tunnel, all your data stay safe, your are 100% protected, no one can see what are you doing, your brother, your friends at work, hotels, conferences or public wifi.
See all plansUsing our PROXY service your internet will be much more secured. All your internet web traffic is scanned automatically to find virus, malwares, ransomwares and others kind of malicious softwares and attacks. You can choose block Porn sites too!
See all plansI am pleased to introduce HACKER<#4+!, the first and only chat in the world that uses PGP encryption for message and files exchange, guaranteeing an unprecedented level of security in the world. Not to be confused with ChatGPT, although it looks similar, our PGP is even better!
See all plansSmart bots powered by artificial intelligence like OpenAI's ChatGPT-4 use advanced algorithms to understand and generate human-like text. These bots can engage in conversations, answer questions, and perform tasks through written dialogue.
See all plansHaving an artificial intelligence like OpenAI's ChatGPT integrated with a command line interface (CLI) for verifying all commands and their outputs (stdout) offers several advantages.
See all plansOur BACKUP service provide security against attackers and provide confidantiality, integrety and disponibility of your data. Even if your backup was stolen or compromise nobody will be able to see the data.
See all plansHOSTING your site with us, you will not only have a safe place to share contents. And if you don't have a domain, you can choose many hosting domains. By default, your site is protect from XSS, SRSF, CSS, JS, and SQL Injection
See all plansALIAS service was created to you who wants to have an e-mail encrypted with a PGP automaticaly and send to another e-mail account 100% secured. And dispited the securety you can choose many fancy hacker & enginner domains.
See all plansHACKER<#4+! CHAT APP
Download Android Version ONLY
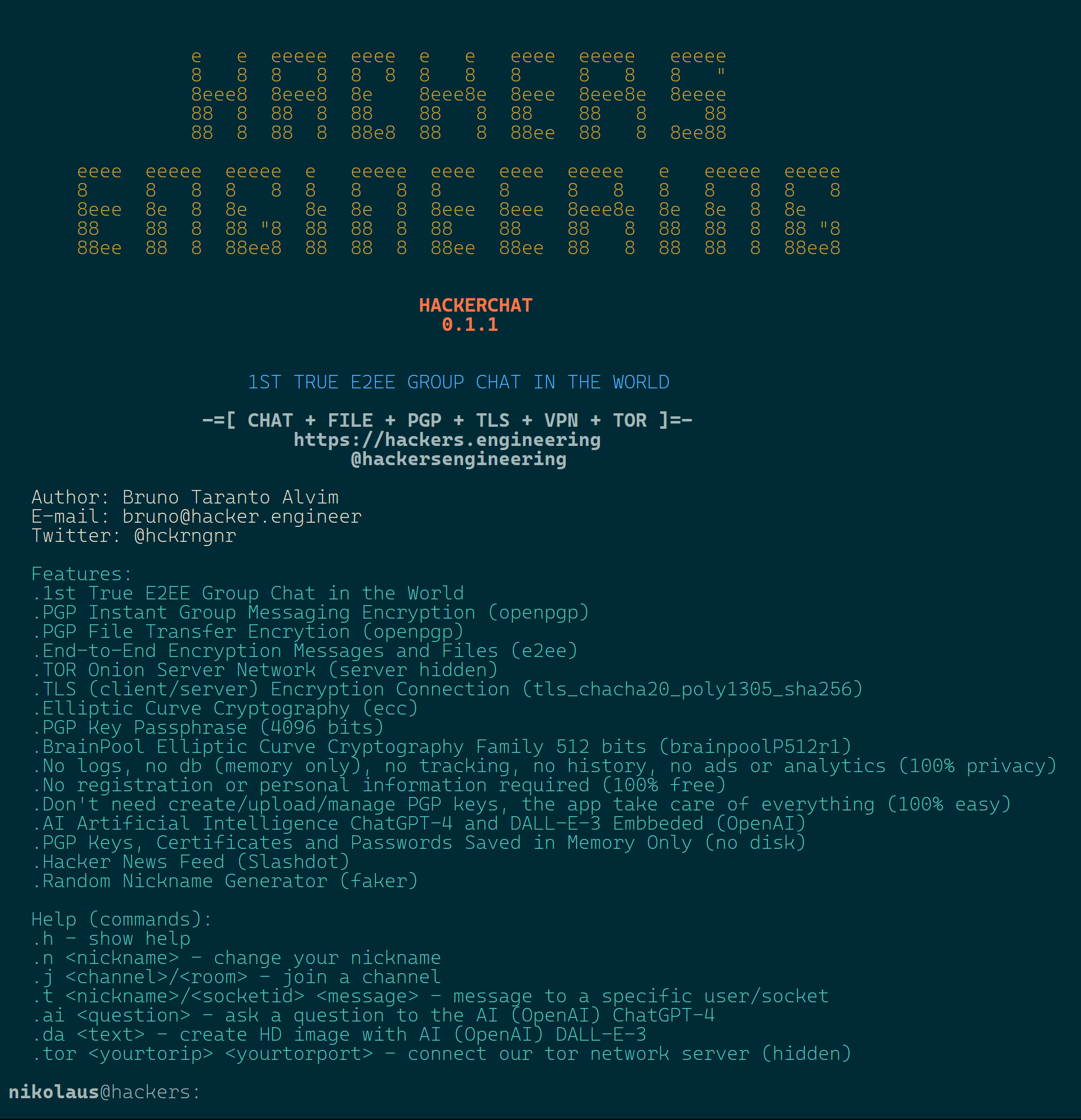
THE ONLY END-2-END-ENCRYPTION CHAT IN THE WORLD
.PGP Instant Group Messaging Encryption (openpgp)
.PGP File Transfer Encrytion (openpgp)
.End-to-End Encryption Messages and Files (e2ee)
.TOR Onion Server Network (server hidden)
.TLS (client/server) Encryption Connection (tls_chacha20_poly1305_sha256)
.Elliptic Curve Cryptography (ecc)
.PGP Key Passphrase (4096 bits)
.BrainPool Elliptic Curve Cryptography Family 512 bits (brainpoolP512r1)
.No logs, no db (memory only), no tracking, no history, no ads or analytics (100% privacy)
.No registration or personal information required (100% free)
.Don't need create/upload/manage PGP keys, the app take care of everything (100% easy)
.AI Artificial Intelligence ChatGPT-4 and DALL-E-3 Embedded (OpenAI)
.PGP Keys, Certificates and Passwords Saved in Memory Only (no disk)
.Hacker News Feed (Slashdot)
.Random Nickname Generator (faker)
- ChaCha20 is an encryption algorithm that provides confidentiality.
- Poly1305 is used for message authentication, ensuring the integrity and authenticity of the data.
- SHA256 is a cryptographic hash function in the Secure Hash Algorithm 2 (SHA-2) family, used for additional data integrity checks.
- TLS 1.3 with ChaCha20-Poly1305-SHA256 is thus a configuration that uses these specific algorithms to secure data transmissions, offering a high level of security and performance, particularly on devices that do not have hardware acceleration for other algorithms like AES.
- Automated Key Generation: When a user starts the app for the first time, it automatically generates a PGP key pair (private and public key) in the background without user intervention.
- Seamless Key Distribution: The app might automatically share the public key with other users or a central repository, making it available for others to use for encryption.
- Transparent Encryption/Decryption: Whenever the user receives or sends a message, the app automatically encrypts or decrypts the content using the appropriate private or public key.
- Key Management: The app handles all aspects of key management, such as key expiration, revocation, and storage, typically using secure elements in the user's device.
- No Manual Uploads: The user does not need to manually upload keys to servers or exchange them with others, as the app takes care of these processes.
By removing the need for manual key handling, such applications make the use of PGP encryption accessible to a wider audience without the need for technical knowledge of cryptography.
- Automated Key Generation: When a user starts the app for the first time, it automatically generates a PGP key pair (private and public key) in the background without user intervention.
- Seamless Key Distribution: The app might automatically share the public key with other users or a central repository, making it available for others to use for encryption.
- Transparent Encryption/Decryption: Whenever the user receives or sends a message, the app automatically encrypts or decrypts the content using the appropriate private or public key.
- Key Management: The app handles all aspects of key management, such as key expiration, revocation, and storage, typically using secure elements in the user's device.
- No Manual Uploads: The user does not need to manually upload keys to servers or exchange them with others, as the app takes care of these processes.
By removing the need for manual key handling, such applications make the use of PGP encryption accessible to a wider audience without the need for technical knowledge of cryptography.
- Conversation and Interaction: You can interact with ChatGPT-4 in a conversational manner, asking questions, seeking advice, or simply chatting. The AI is designed to respond in a human-like way, making the interaction engaging.
- Information Retrieval: ChatGPT-4 can help you find and summarize information from a vast knowledge base it was trained on, up to its last update in April 2023. You can ask it for explanations on a wide range of topics.
- Problem-Solving: If you encounter issues or need to troubleshoot something, the AI can provide step-by-step guidance based on best practices and its understanding of common solutions.
- Learning and Education: The AI can assist with learning new concepts, explaining difficult subjects, or providing examples and analogies to help you understand complex topics.
- Entertainment: It can generate stories, jokes, or even come up with games to play, providing entertainment and a way to pass the time.
- Programming Help: For platforms like HACKER<#4+!, where many users may be programmers, ChatGPT-4 can offer coding assistance, debug code snippets, or discuss programming concepts.
- Creative Assistance: The AI can help generate ideas, write creative content, or provide feedback on written work.
- Language Translation: It can translate between languages, making communication easier on international platforms.
- Accessibility: ChatGPT-4 can make technology more accessible by offering an intuitive conversational interface that may be easier for some users than traditional UI elements.
By integrating ChatGPT-4 into a chat platform, users gain a versatile tool that can enhance their online experience in many ways, from improving productivity to simply having a fun conversation.
- Visual Aid: Users can generate images to aid in explanations, whether they're discussing concepts, demonstrating ideas, or sharing creative thoughts that are easier conveyed through visuals.
- Custom Emojis and Stickers: DALL-E 3 could create personalized emojis or stickers on the fly, allowing for a more expressive and unique chatting experience.
- Educational Illustrations: When explaining educational content, DALL-E 3 can provide illustrations to accompany explanations of difficult concepts, making learning more interactive and engaging.
- Creative Collaboration: For discussions that involve design, art, or creativity, users can collaborate in real-time, using images generated by DALL-E 3 to visualize concepts or iterations of creative projects.
- Debugging Assistance: In tech-related chats, users can describe a problem and use DALL-E 3 to generate an image of what they think is happening, which can help in diagnosing issues or explaining them to others for assistance.
- Enhanced Storytelling: When sharing stories or creating narratives, DALL-E 3 can be used to create visual scenes, characters, and settings, enriching the storytelling experience.
- Prototyping: For discussions around product design or development, DALL-E 3 can quickly generate visual prototypes based on descriptive inputs, facilitating brainstorming and iteration.
- Memes and Humor: Users can create memes or humorous images in real-time, adding a layer of entertainment and fun to the conversations.
- Language Learning: In language learning contexts, visual aids can be incredibly helpful, and DALL-E 3 can provide images that help explain the meaning of words or phrases in different languages.
By embedding an AI-powered image generation tool like DALL-E 3 into a messaging platform, users are empowered to enhance their communication with visual content, making interactions more vibrant and multifaceted. It can foster a more immersive and engaging chat experience, blending the richness of visual content with the convenience of text-based messaging.
Migrate your Inbox
Make us your default e-mail and domain provider

Secure your online privacy with VPN
You have online rights, use them

Fell Free
We believe privacy and security are fundamental human rights, Unlike other VPNs, there are no catches. We don't serve ads or secretly sell your browsing history.
Easy to Use
The best security tools in the world will only protect you if used correctly and consistently. We have extensively simplified the VPN interface to make it as intuitive as possible – so you can stay protected every day, hassle free.
Fast VPN Speeds
A 10 Gbps server network combined with our unique suite of VPN technologies can improve speeds by over 400%. The advanced network TCP flow control algorithm we utilize provides unparalleled performance and connection stability.
Defenses Agains Email Attacks
See a list

People are the weakest link in any security system, which is why we have added several layers of defense against social engineering attacks and human error. Best of all, these features don’t require any extra steps. Your inbox is secured by default.
Protect yourself against mass surveillance from government agencies like the NSA by using a private email provider like we. We don’t have access to your email messages, so we can’t hand them over to any government agency.
Unlike other email providers, we don’t hold the decryption keys for your emails. This means that your messages can’t be decrypted, even if our servers were hacked. If you use Proton Mail, you’re less vulnerable to email server hacks like the Microsoft Exchange hack of 2021.
We are funded by subscriptions to our paid plans, not by invading your privacy and serving you advertisements. Unlike other email services, we have no motivation to use your data to deliver surveillance-based advertising in your inbox.
Why choose Hacker Engineering
Below we list some advantages of choosing Hackers & Engineers
You are encrypted under the VPN connection, you are encrypted under the e-mail SSL/TLS connection and you are encrypted under the PGP cryptography.
You are safe inside the VPN Hacker Engineering Network, all your traffic is encrypted. Discover all the benefits to be under our protection. You are safe to navegate in the internet.
You can use our proxy to speed up your already hidden encrypted connections. All cache of the sites and images of the sites you access is already cached, speeding up your internet access.
Using our proxy caching server you can choose to block pornography connections and keep your family safe. You don't need to worry about what is outside.
Yes! We are connected to the TOR Onion network. You can access our services (email, proxy, xmpp, vpn, ...) over TOR Onion network!
Your connections is automatically firewalled under the VPN. Nobody can access your computer, even if he is already compromised.
We're here to secure you with whatever you need. Don't exitate to contact us You can use XMPP too.
When you are connected to the VPN, your provider, your company, cannot tracking or sniff your connection, everything is encrypted. Our servers is configured to avoid all logs.
_\|/_
Your connection is safe out of USA. Everything you do exit to the internet in Amsterdam. When you connect the VPN or use our Proxy, is like you are in Amsterdam!
_\|/_
You can choose many domains to best expreess your purposes, for fun or profit. No matter what is your goals, we are here to protect you.
Pretty Good Privacy. All e-mails come with a PGP key to protect not only your e-mails, but you can use the same PGP key to protect documents, any kind of files, Bitcoins and etc.
No matter what computer, laptop, cellular, operational system, E-mail Client, Outlook, Thunderbird, K-9, Windows, Android, Mac, Iphone, FreeBSD or Linux, our solution works on all platforms, you will be secured everywhere, anywhere, anytime. Our solutions feets all technologies.
Don't worry about your IP, we hide for you. We expose our IP to protect yours from the Internet. Nobody can knows where you are or who are you in the world. You can be at the moon!
Our domain name servers are configured with the lastest security technologies. Your e-mails are protect from spammers and scammers, we use DNSSEC, DKIM, DMARC and SPF.
We choose the most secure operation system in the world to host our services. All servers are running under the OpenBSD. We choose security first, and second we choose the security, and third security, and so on.
Whatsup, Telegram, Facebook, Twiiter, ..., all this techonologies are compromised already and don't offer end-to-end encryption. We have our own solution, we have our own secure IM Message solution, we use encrypted XMPP.
Our emails servers not only encrypt your emails but have the capability to scan all emails you send and receive to serch for vírus, spam, malwares, files suspicius and ransonwares.
You can talk and see your friends under the VPN network 100% secure! Nobody will know you are talking or doing a video call with your bodies! No big brother here!
Your provider, your company or even your brother hacker who lives under your house will never know what sites you are browsing, messaging, calling, talking, ... Everything is encrypted under the VPN, you and what you are doing are completely hidden from everybody.
Nobody can censor you or your connections Nobody can block you. Nobody knows what you are doing, you are hacker engineer, you are hidden like a ninja.
We provide hacking, engineering, security and tech news over e-mail and directly in our message solutions. We broadcast messages related with security to you to be up-to-date about what is going on.
Your e-mails is secured with our daily backup. Our backup is encrypted using your own PGP key with 4096 bits. Only you can open the backup.
We can forwaed all e-mails to another e-mail account outside our servers, like Gmail, Hotmail, Business, ..., encrypted with your own PGP key. Nobody will see your e-mails! Never!
You can talk with your friends security under VPN. We have a Hackers Enginneers Group where you can meet other professionals and people anytime you want! Whatsup and Telegram groups never more! Let's chat privately!
Don't trust the hosting company are you using? So do we! You can use all services using your own domain(s).
We love Mutt! The best e-mail client on the planet! We will share our config with you to you to have your cool hacker e-mail client. You can use under the VPN or under the TOR network, encrypted and securely.
We provide many security tools to you take care of your computer, your connection and your network, including personal alerts. We will give tips and tricks too!
To sign a message, the sender uses their private key to create a digital signature. The recipient can then use the sender's public key to verify the signature and confirm the authenticity of the message.
A
C
K
T
H
E
P
L
A
N
E
T
Fun and Profit
Choose the best E-mails domain to express your online personality.
Are you a Hacker? Are you a Engineer? Or are you a hacker and engineer?
Are you a Red Team? Are you a malware hunter? Are you a biologist? Are you a low level programmer? Bug hunter?
Are you feel like a CyberPunk?
Are you the best of the best engineer? Like the engineer boss? The patron?
Are you a very bad engineer? Like to burn?
Are you a radio frequency engineer? Are you like radio stuffs? Are you a radio amateur? Like to broadcast?
Are you a reverse engineer? A bug bounter? Like to reverse things? Then you need a .re email.
You like to have a fun e-mail? We are here for fun and profit! :)
You like to have a fun e-mail? We are here for fun and profit! :)
Do you thinkg this host defines your online personality? Want to have an email like you@cyberpunk.hacker.enginner?
Do you thinkg this host defines your online personality? Want to have an email like you@phreak.hacker.enginner?
Do you thinkg this crazy host defines your online personality? Want to have an email like you@reverse.hacker.enginner?
Our private engineer domain! Only works under the VPN! Good to have a 100% of secure communications with your hackers engineers friends! 100% hidden from the world! No .com or .anything! Your e-mail is you@ENGINEER
Our private hacker domain! Only works under the VPN! Good to have a 100% of secure communications with your hackers engineers friends! 100% hidden from the world! No .com or .anything! Your e-mail is you@HACKER
Our private me domain! Only works under the VPN! Good to have a 100% of secure communications with your hackers engineers friends! 100% hidden from the world! No .com or .anything! Your e-mail is you@i
AI Shell ChatGPT Embedded
Why use AI Shell?
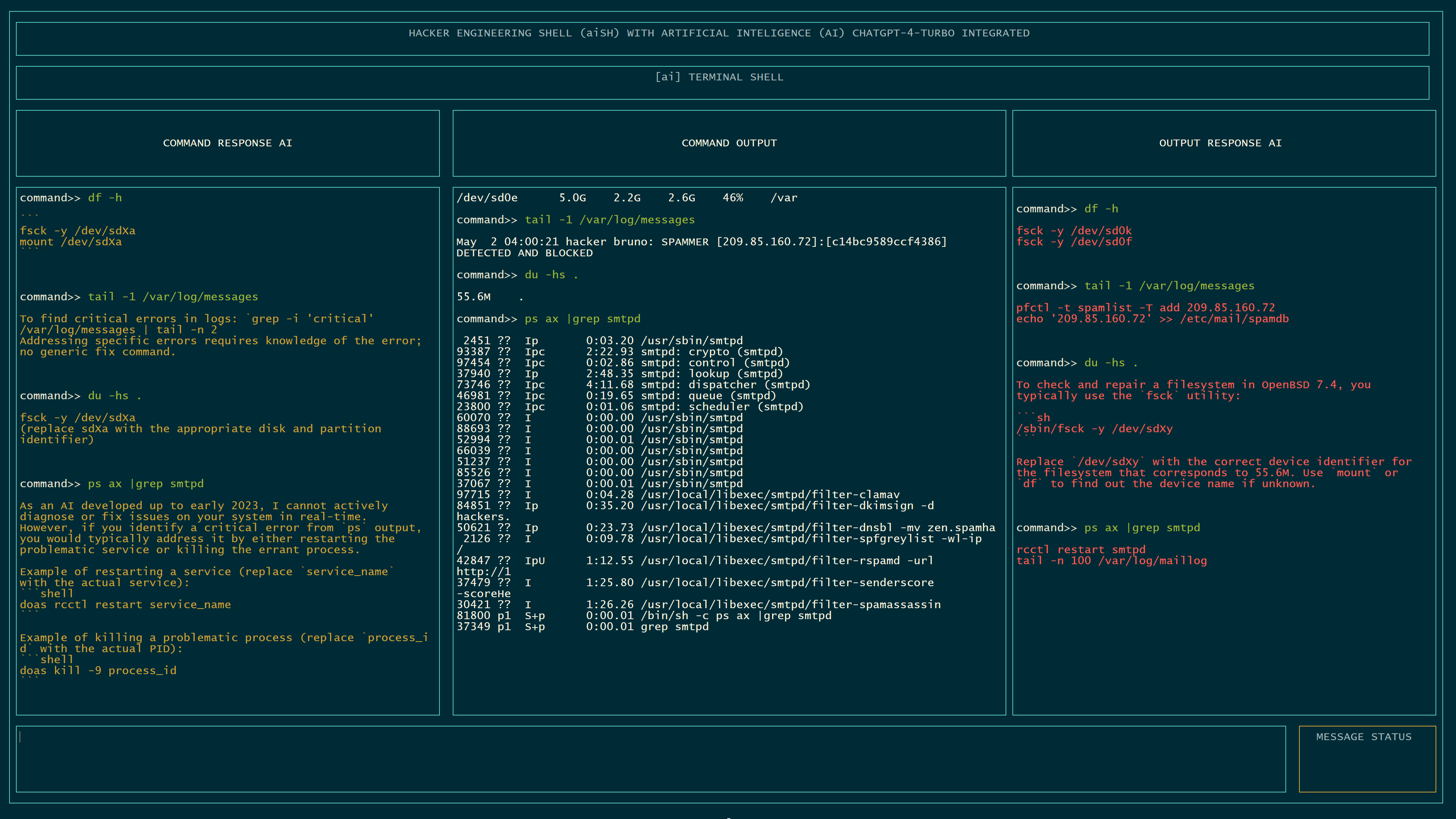

The integration of OpenAI's ChatGPT with a command line interface (CLI) represents a significant advancement in the usability and functionality of traditional command line environments. In this integrated system, ChatGPT serves as an intelligent intermediary between the user and the CLI, providing real-time assistance and feedback.
A selection of operating systems to choose from
Our products and services allow you to select your preferred Operation System






Our VPN is available on all your devices, including PCs, Macs, smartphones, and even routers. A secure Internet connection that you can trust is essential to maintaining your privacy on your laptop at home, your mobile device on the road, or your workstation at the office. Our VPN has native apps for all plataforms.
AI Smart and beautiful Robots (BOT's)
They are Inside












AI SMART BOT FEATURES
- Translation in Real-Time: They can translate messages between different languages as they are sent and received, allowing users to communicate across language barriers.
- Content Moderation: They can monitor conversations for hate speech or other unwanted content and take actions such as alerting moderators, deleting messages, or providing warnings.
- News Delivery: Users can request the latest news, and the bot will fetch and relay the information in the chat.
Such bots can greatly enhance the functionality and user experience on messaging platforms, making them more accessible, safer, and informative..
We are connected to the TOR Network
Below a list of benefits
Tor is free, open-source software for enabling anonymous communication. When you connect to the internet via Tor, your internet is routed through a worldwide, volunteer network of relays that conceal your location and activity from anyone trying to monitor you.
Why use Tor?Using Tor to access Proton is optional, but in some situations it may bring additional security benefits. Instructions on how to use our Tor encrypted email or Tor encrypted file storage access can be found here(new window). More information about how Proton uses Tor to protect your privacy can be found here(new window).
Our Tor Hostfymtsmpy6nt5nsgamwc6xsto545fllm6waawua7wsaqiwgger5kzh7ad.onion
Keep in mindUsing Tor does come with some downsides. Tor connections typically deliver much slower and less reliable performance than a standard internet connection.
Even without using Tor, Our's services are secured with end-to-end encryption, secure authentication (SRP), and optional two-factor authentication. Most people will not need to use our Tor encrypted email or Tor encrypted file storage access. However, if you are an activist in a sensitive situation, our onion site provides an extra layer of anonymity and protection.
Plataforms CompatibilityTor is available for all operational system and all phones.


Hacker Engineering was founded by BRUNO TARANTO, located in Silicon Valley (California) in order to provide the State-Of-The-Art in Information Security for its partners and customers, for Hackers Engineers. BRUNO TARANTO is a Hacker and Engineer, has a Bachelor in Electrical Engineering, a Radio Frequency Engineering Certification from University of California San Diego (UCSD), incomplete Master Degree (unfortunately) in Applied Electromagnetism (Military Institute of Engineering) and a long (25 years) Cyber Security Engineering Career. Starting his career as SysAdmin of his own Internet Dial-Up Provider and responsable for others 2 Internet Dial-Up Providers, one of them the biggest at the time (20 years ago). Proud to have been the Internet Manager in his birth State, responsible for the entire State's Internet Infrastructure. Worked as security engineer in telecom company, the biggest, with millions of customers, was resposible for thousands of VPNs, site-to-site and client-to-site. With strong knowledge and experience with the biggest security players and solutions in the world, including CISCO, CheckPoint, Fortinet and BlueCoat, which he has the Symantec / Bluecoat (CheckPoint) X-Series Certificated Specialist. Pioneered in Vulnerability Analysis and Penetration Testing in telecommunication companies, in the late 1990s, and working as Security Engineer to the biggest companies in the world.
Hacker Engineer Search
Google and Bing don't need to know what are you looking for.
Do a safe search under the VPN TOR ONION NETWORKS. 100% Safe.
Our customers trust us
See a list of trusted customer testimonials

VPS is the most valuable trading asset we have ever purchased. We cannot understand how we live without VPS.

It's really wonderful. If you want real marketing that works and an effective implementation, OnbleyServers shared hosting offers the solution.

I highly recommend OnbleyServers VPS Servers to all companies interested in running a successful online business for little!

VPS is the most valuable trading asset we have ever purchased. We cannot understand how we live without VPS.

About Us
Hacker Engineering is a hosting company that offers security hosting services, like email, vpn, site, internet messenger, proxy and many other services to keep you and your business safe.
We are committed to providing the State-Of-The-Art in Information Security. We will be happy to help you solve your security problem or boost your security online business..
Our Solutions, but Not Limeted
Some of our technologies and solutions


























